- BT Community
- /
- Archive
- /
- Archive Staging
- /
- Scam Alert! Scam missed delivery texts and Flubot ...
- Subscribe to this Topic's RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Subscribe to this message's RSS Feed
- Highlight this Message
- Report Inappropriate Content
Scam Alert! Scam missed delivery texts and Flubot Malware
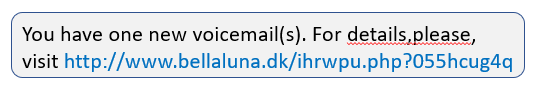
Flubot malware is malicious software that is installed when a victim receives a text message and follows a link, asking them to install a tracking app. This could be informing them of a "new voicemail" received or a ‘missed package delivery’. The tracking app is in fact spyware that steals passwords and other sensitive data and then also sends out multiple text messages to further pass on the malware.
We will be sending text messages to customers that we have identified as being impacted by this scam, the text messages will link to this community article and we have including the contents of the text below so that you know it is genuine.
How can I spot this particular scam
Victims receive a text message with a link asking them to install an app either for a new voicemail or a ‘missed package delivery’. See examples below for each of these, however, the message and app/link may vary and reference any company.
What happens to my phone if I install Flubot Malware?
The Flubot malware impersonates other apps on a victim’s phone to steal their banking credentials and other private information. It will also access contact details and send out additional text messages – further spreading the spyware. It can eavesdrop on incoming notifications, read and write SMS’, make calls, and transmit the victims’ entire contact list back to its control centre.
If you receive a scam text message:
- Do NOT click the link in the message, and do not install any apps if prompted.
- Forward the message to 7726, a free spam-reporting service provided by phone operators.
- Delete the message.
If you have already clicked the link to download the [Flubot] application:
The NCSC (National Cyber Security Centre) have released guidance on what to do if you receive a Flubot SMS. You can find out more from the NCSC HERE.
How to protect yourself
You must clean your device, as your passwords and online accounts are now at risk from hackers.
- DO NOT enter your password, or log into any accounts until you have followed the below steps.
- To remove any Malware from your device you should
Perform a factory reset as soon as possible. The process for doing this will vary based on the device manufacturer, and guidance can be found here.
Note that if you don't have backups enabled, you will lose data. - Protect any online accounts
If you have logged in to any accounts or apps using a password since downloading the app, that account password needs to be changed. - If you have used these same passwords for any other accounts, then these also need to be changed.
To protect yourself from future scams like this, you should
- Back up your device to ensure that you don't lose important information like photos and documents. The CyberAware campaign explains how to do this.
- Only install new apps onto your device from the app store that your manufacturer recommends. For example, most Android devices use Google's Play Store. Some manufacturers, such as Huawei, provide their own app store.
- For Android devices, make sure that Google's Play Protect service is enabled if your device supports it. Some Huawei devices provide a similar tool to scan devices for viruses. This will ensure that any malware on your device can be detected and removed.
If you are using a different SMS client to Google messages which does not include spam protection you might want to switch to one with integrated spam protection or install a third-party security solution from Google Play that can filter incoming spam SMS before it hits.
Users on Google Chrome, Firefox, and certain other web browsers are protected by Google’s Safebrowsing technology that shows a warning when a user browses to a known Flubot distribution site. If you are not using one of these you might want to consider using a browser with Safebrowsing or similar website scanning technologies from other vendors.
More about Google Safebrowsing can be found Google Safe browsing